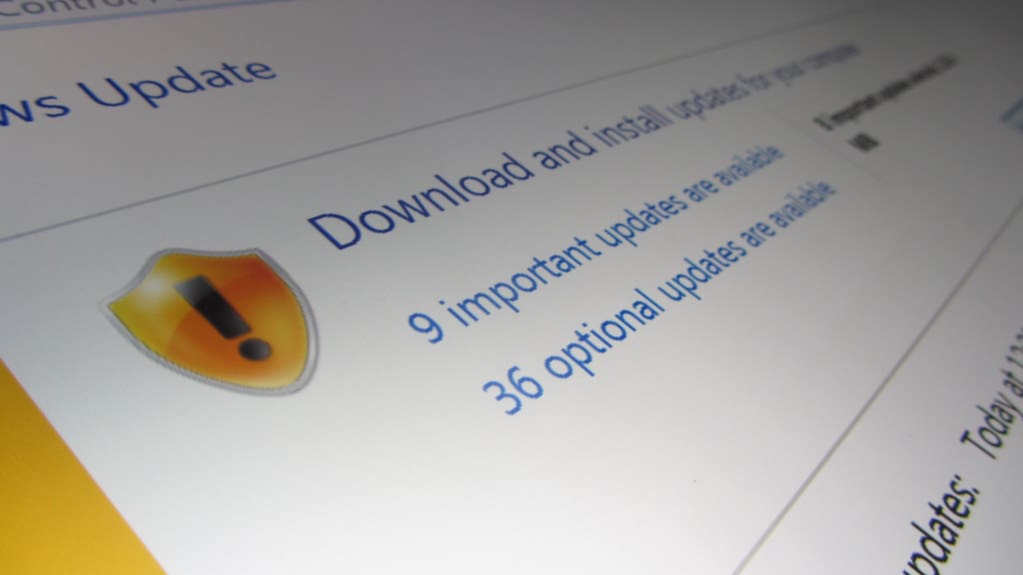
Microsoft released its February 2026 Patch Tuesday security updates on February 10, 2026, fixing 58 vulnerabilities across Windows, Microsoft 365, Office, and related components — including six zero-day vulnerabilities that were being actively exploited by threat actors in the wild before patches were available. Security professionals and enterprise IT teams were urged to prioritise immediate deployment given the severity and active exploitation of the critical flaws.
Of the six zero-days, three — CVE-2026-21513, CVE-2026-21510, and CVE-2026-21514 — had been publicly disclosed prior to patching, meaning detailed exploitation techniques were potentially available to a broad range of attackers including less sophisticated groups who typically require public proof-of-concept code before attempting attacks. The remaining three were addressed before public disclosure, suggesting Microsoft received private notifications from security researchers or intelligence partners detecting exploitation in targeted campaigns.
CVE-2026-21513 represents a critical MSHTML Framework security feature bypass that allows unauthorised attackers to circumvent protection mechanisms remotely over a network. The MSHTML component, which powers Internet Explorer legacy features embedded in various Windows applications, has historically been a high-value target because it processes web content in contexts where users may not expect browser-grade security controls to be active. Microsoft attributed discovery to a collaboration between its own Threat Intelligence Center, Security Response Center, Office Product Group Security Team, and Google Threat Intelligence Group — an unusual consortium suggesting coordinated tracking of a sophisticated threat actor.
CVE-2026-21514 targets Microsoft Word, exploiting vulnerabilities in how the application handles OLE (Object Linking and Embedding) components embedded in Office documents. Attackers must deliver malicious Office files to victims and convince them to open the documents, making this a spear-phishing vector particularly dangerous in corporate environments where opening emailed documents is routine.
The February update also addresses the beginning of Microsoft’s Secure Boot certificate rotation programme. The original Secure Boot certificates issued in 2011 are scheduled to expire in late June 2026, requiring all Windows devices to receive updated certificates through a carefully staged rollout designed to prevent boot failures on devices with compatibility issues. Microsoft has implemented a targeting mechanism using device telemetry to identify systems with sufficient compatibility signals before delivering new certificates.
Additional vendors releasing coordinated security updates in the February cycle include Adobe (Audition, After Effects, InDesign, Lightroom Classic), BeyondTrust (critical remote code execution flaw in privileged access management software), Cisco (Secure Web Appliance, Meeting Management), and Fortinet (FortiOS and FortiSandbox). CISA simultaneously issued a binding operational directive requiring US federal agencies to immediately remove network edge devices that have reached end-of-support status — reflecting growing concern about threat actors systematically targeting unpatched legacy infrastructure at government perimeters.
Security practitioners highlighted the February patch load as unusually significant, recommending organisations implement an emergency patching cadence for the six zero-days rather than waiting for standard monthly maintenance windows. Endpoint detection and response platforms are expected to release detection content for the newly patched vulnerabilities within hours of the disclosure.